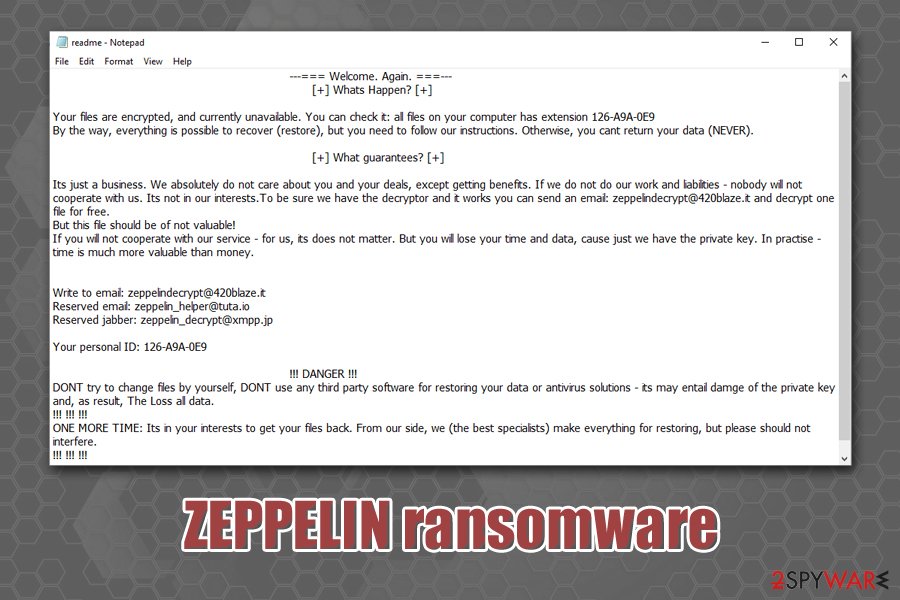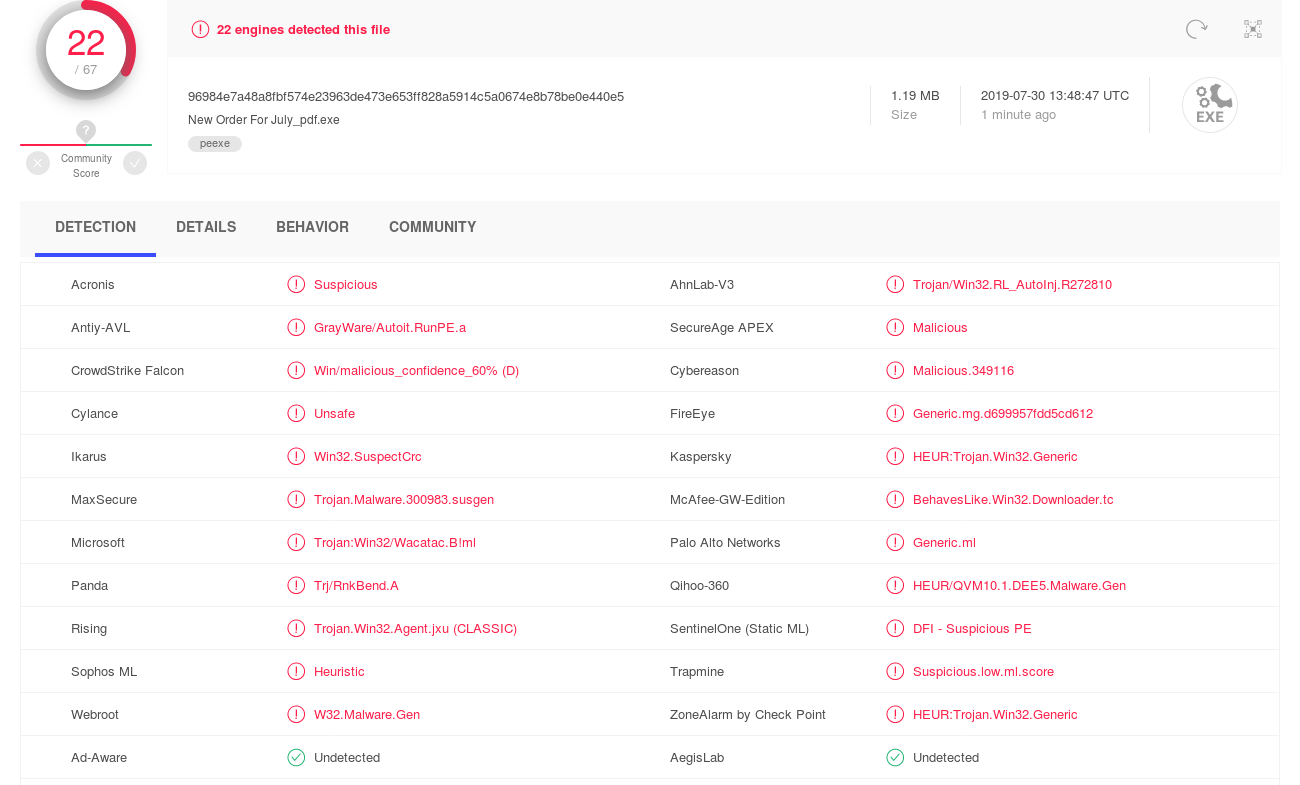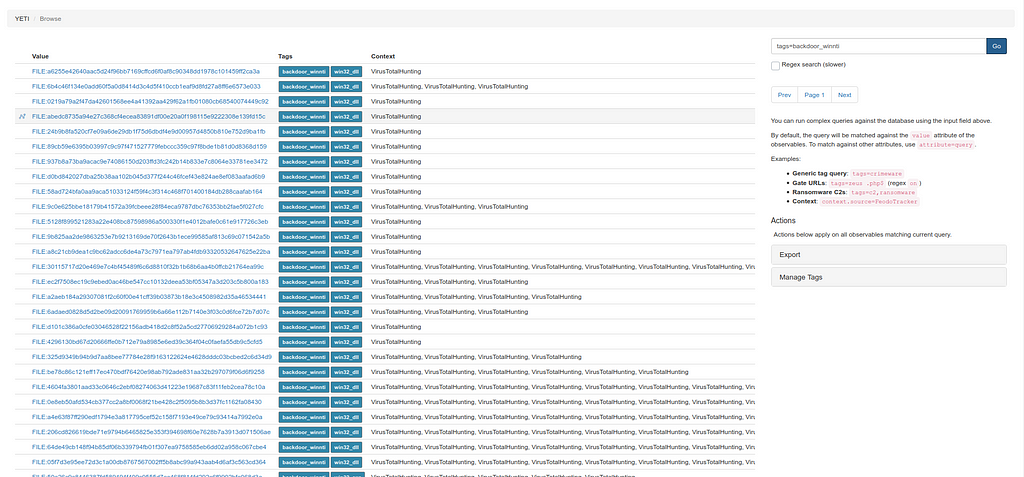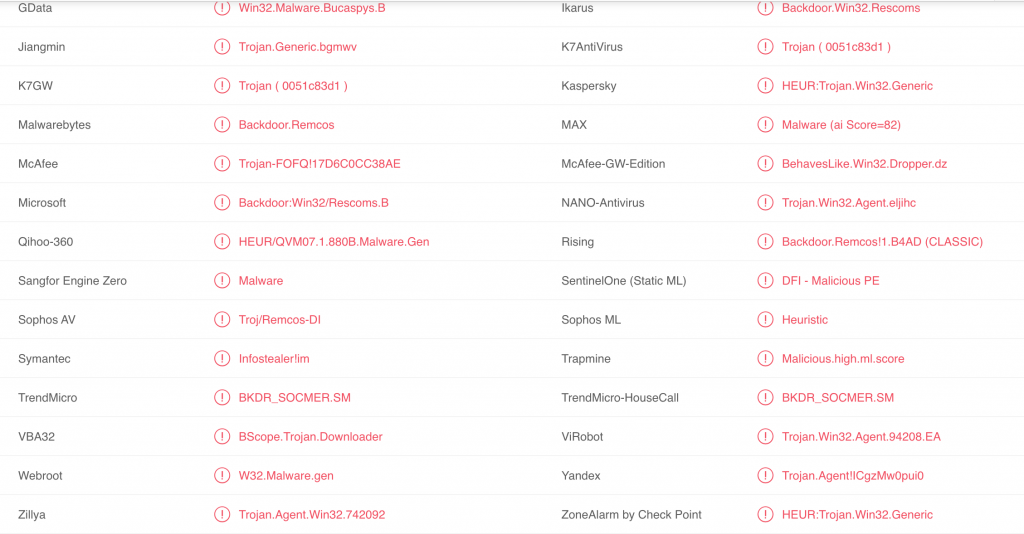
Malware analysis https://labs.inquest.net/dfi/search/hash/sha256/0c91fa2d30e1981d8ac276ecaacb4225c3bef5be8143597720e37e7dc5447099 No threats detected | ANY.RUN - Malware Sandbox Online
Automated Malware Analysis Report for https://hs-6832097.s.hubspotemail.net/hs/manage-preferences/unsubscribe-all?d=VndZ7w9lmXBxVPkYN343Tw8KW3K6hGQ2m9rSFW43X00B43XQ2QW8kDfTY17f7hvW7-1xwN4-dMDLW4WpGqv5rbWS_N51wb2m28RMvN6CM05CGKd_PV20N5Z7vPVldW2fb0h ...
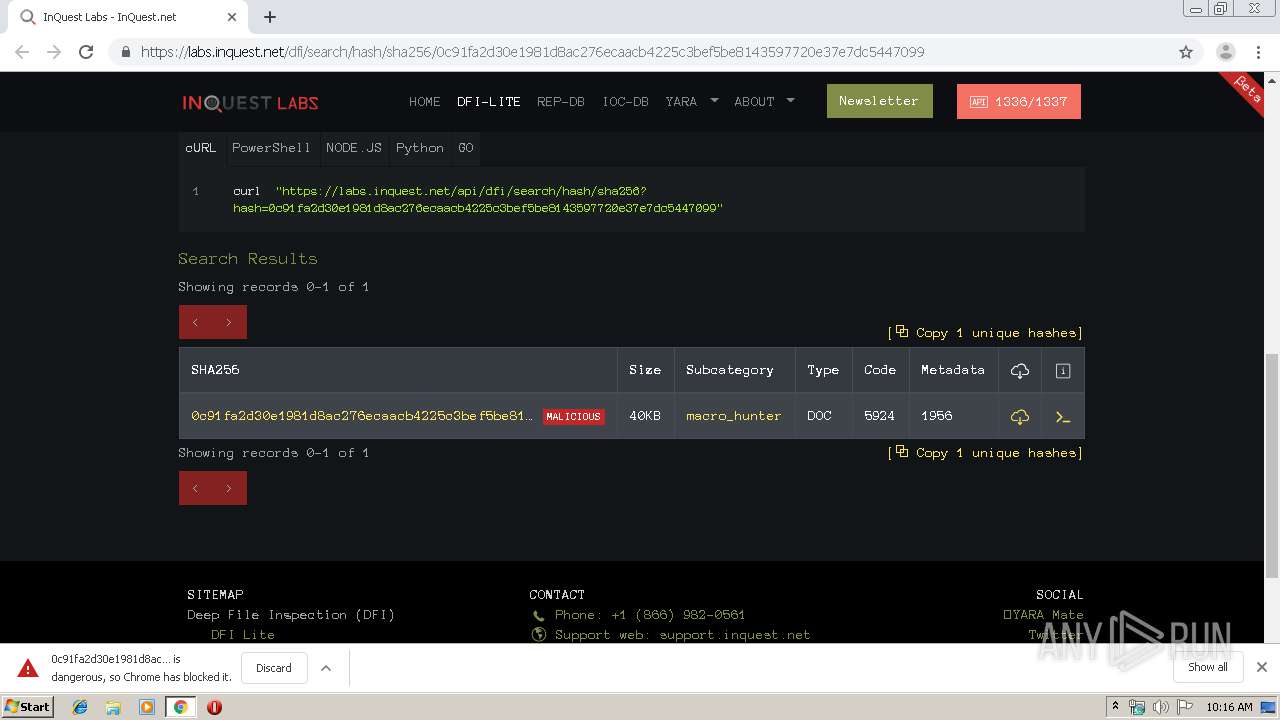
Malware analysis https://labs.inquest.net/dfi/search/hash/sha256/0c91fa2d30e1981d8ac276ecaacb4225c3bef5be8143597720e37e7dc5447099 No threats detected | ANY.RUN - Malware Sandbox Online

Samir on Twitter: "pivoting on rwdrv.sys (legit signed driver to discover UEFI other HW related settings) leads to Lojax/DoubleAgent UEFI rootkit. sysmon check eventid 6 with Signature: "ChongKim Chan" (cuz there are
Automated Malware Analysis Report for https://diversifiedfeedback.co1.qualtrics.com/jfe/form/SV_0cfSGjQsqIKx3tb?Q_DL=B5hDHc4IJE7pjyk_0cfSGjQsqIKx3tb_MLRP_bIsJJD2b2R5AFYV&Q_CHL=email - Generated by Joe Sandbox